

Discover Vulnerabilities and Exploit Them
In the era of Al vs. Al, we're here to buid your fortress of security ahead of time
HackBox (Virtual Attacker Bot) is an automated penetration testing platform that integrates AI with both offensive and defensive cybersecurity techniques.
By simulating real-world attacks, HackBox empowers organizations to proactively identify and address exploitable vulnerabilities within their digital assets — before malicious actors can exploit them. This offensive simulation approach enhances cyber resilience, provides a tactical edge in threat response, and significantly reduces network security risks for enterprise operations.
See a Demo Now
Automatically identifies attack vectors such as open ports and services, web fingerprints, URLs, admin login portals, and file upload interfaces.

Automatically detects and verifies various vulnerability of the system and web application.

Automatically generate vulnerability exploit payloads to simulate real-world attacks, realizing the simulated attacks on target systems and risk forensics.

Employs autonomous decision-making to explore all possible attack paths, executing iterative exploits and lateral movement across the environment.

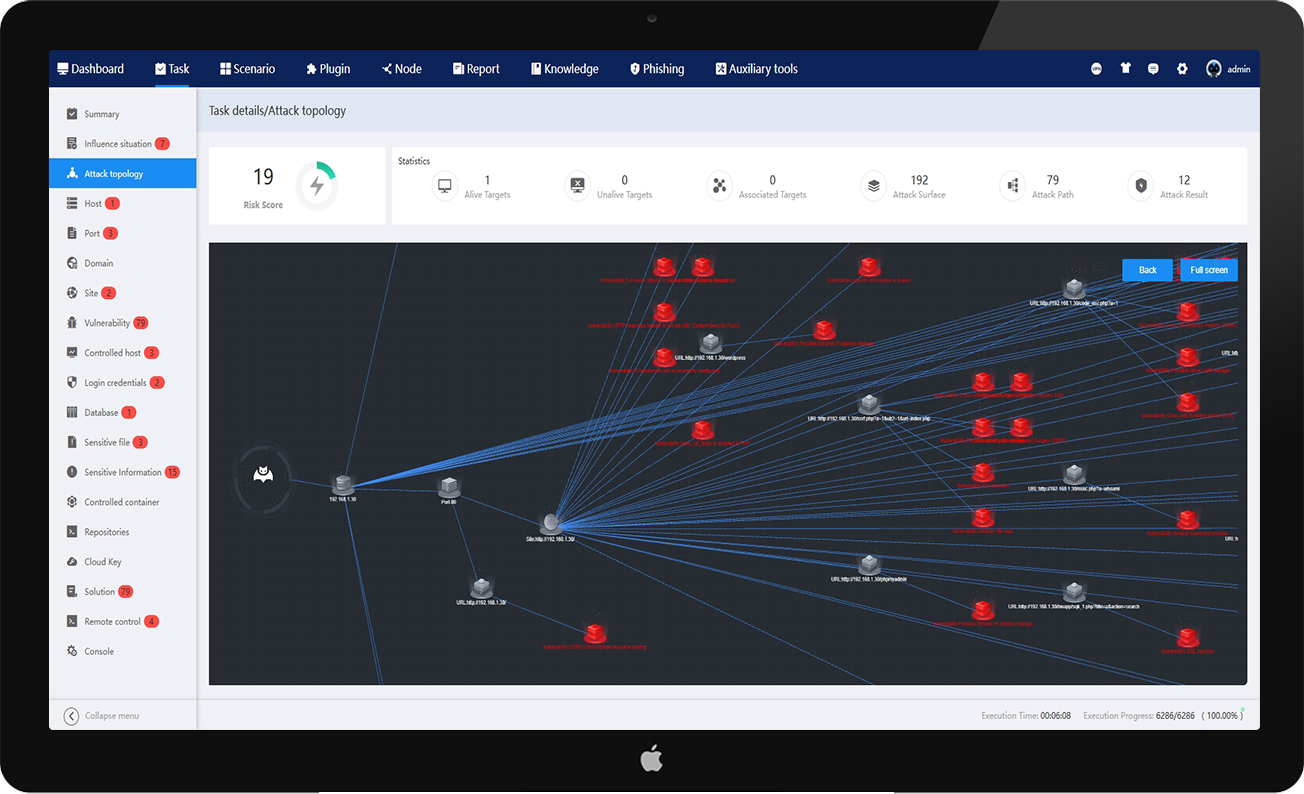
Visualizes the full attack chain, clearly illustrating the penetration process and pinpointing critical risk areas.

Based on vulnerability-driven principles, the system accurately detects and verifies a wide range of vulnerabilities, ensuring reliable results and generating high-quality penetration testing reports for users.

The automated penetration testing is powered by an AI engine that autonomously analyzes collected information and dynamically determines the next steps, including attack paths and actions, throughout the testing process.

Based on the data generated during the penetration testing process, the entire attack lifecycle is reconstructed and presented in a visualized manner, offering an intuitive depiction of both the overall attack landscape and detailed procedural steps.

Based on the data, privileges, and actual outcomes obtained through penetration testing, conduct a quantitative evaluation of risk and provide recommendations on the prioritization of vulnerability remediation.
HackBAS is an automated cybersecurity validation platform that integrates breach and attack simulation (BAS) technology. It provides users with continuous, automated simulation capabilities to validate the effectiveness of security controls and assess the organization's cybersecurity posture, enabling ongoing improvement of defensive capabilities.
See a Demo Now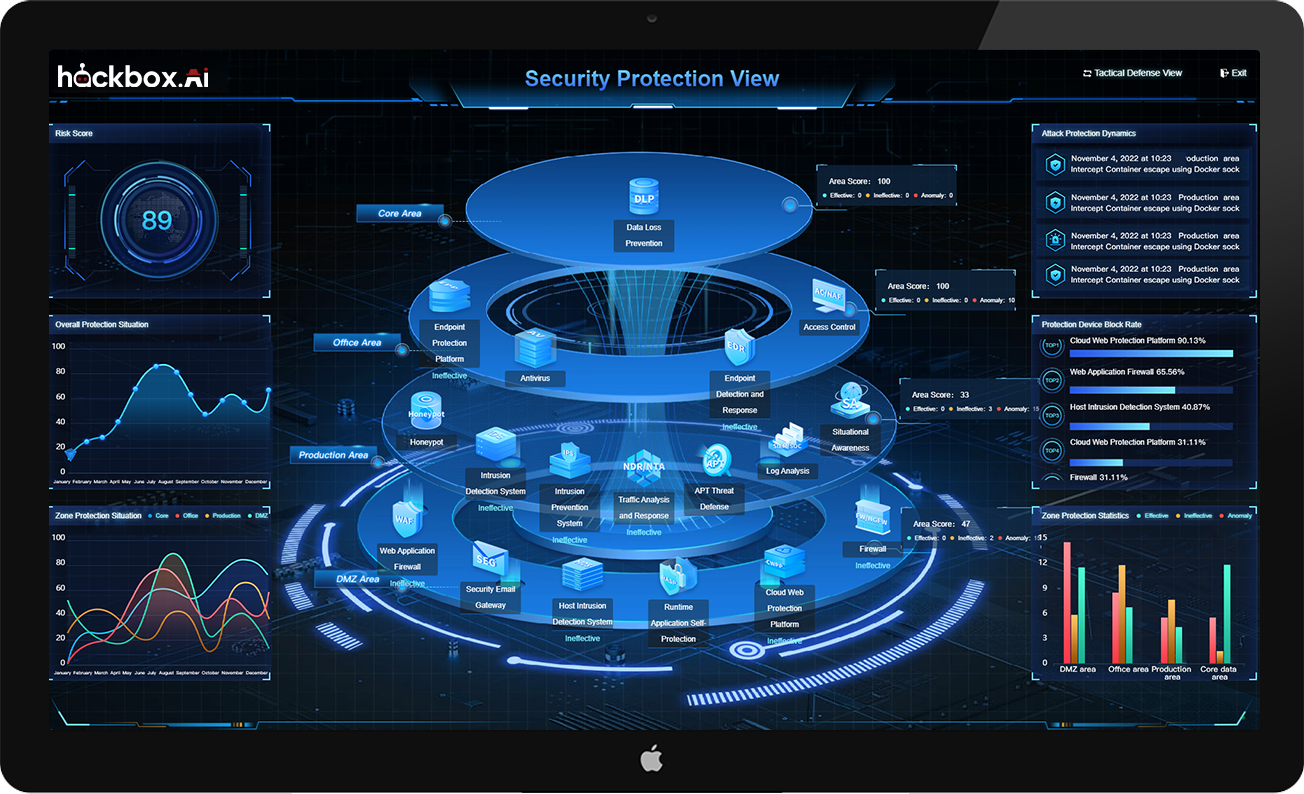
Conduct comprehensive testing and verification of the effectiveness of cybersecurity measures, configurations, and policies across various domains, including data security, endpoint security, web security, email security, and perimeter defense.
Provide actionable recommendations to address security vulnerabilities and weaknesses, enhancing the overall effectiveness ofcybersecurity defenses.
Simulate various APT attack techniques to replicate a full kill chain, from initial infiltration and lateral movement to data exfiltration, conducting comprehensive risk testing across both network and business security.
Evaluate and visually present the defense posture from multiple perspectives, including security defenses, business operations, and attack tactics/techniques.
Automated operation that continuously assesses weaknesses and changes in thesecurity defenses of business and network infrastructure, driving ongoing improvements in thesecurity posture.
Leveraging years of experience in real-world offensive and defensive operations, carefully designed attack scenarios, and a rigorous testing and validation process, HackBAS delivers accurate and reliable results.
Provides a comprehensive assessment of the defense-in-depth system, helping security operations teams identify gaps and key risks in the cybersecurity defense system.
A quantitative assessment of an organization's current security defense level, considering factors such as the difficulty, likelihood, and effectiveness of security threats and defenses, providing a data-driven basis for decisions related to cybersecurity planning, development, and optimization.
